Server configuration and management
<< Installing Firebird | Firebird 2.5 Quick Start Guide | Working with databases >>
Server configuration and management
There are several things you should be aware of – and take care of – before you start using your freshly installed Firebird server. This part of the manual introduces you to some useful tools and shows you how to protect your server and databases.
User management: gsec
Firebird comes with a command-line user management tool called gsec. Although its functions can also be performed by a number of third-party GUI utilities, you should at least have a basic knowledge of gsec, since this is the official tool and it's present in every Firebird server installation. In the next sections you will use gsec to execute three tasks: changing the SYSDBA password, adding Firebird users and (optionally) appointing coadministrators. First though, some points of attention:
Permission to run gsec
gsec if you are logged into the operating system as Superuser (root on Linux) or as the user the Firebird server process runs under. On Windows server platforms, you typically need to be in the Power User group or higher to run gsec successfully.
Trouble running gsec
gsec results in a message like "cannot attach to password database - unable to open database":
- You may be running Firebird on Windows and for some reason the local protocol isn't working. One rather common cause for this is running Windows with Terminal Services (Remote Desktop Services) enabled and connecting to the server from a different session. To enable the local protocol, open
firebird.conf, uncomment theIpcNameparameter and set it toGlobal\FIREBIRD. Then restart the server.
Global\ to the IPCname if the connection fails because of insufficient permissions, so this should not happen anymore.
- If the above doesn't apply to you, you can at least circumvent the problem by "tricking"
gsecinto using TCP/IP. Add the following parameter to the command line, adjusting the path if necessary:
-database "localhost:C:\Program Files\Firebird\Firebird_2_5\security2.fdb"
security2.fdb is the security database, where Firebird keeps its user account details. It is located in your Firebird installation directory.
- Maybe your security database is a renamed
security.fdbfrom Firebird 1.5 or earlier. Of course this can't be the case immediately after installation.
"Cannot attach to services manager", the server may not be running at all. In that case, go back to Testing your installation and fix the problem.
Invoking gsec on Linux
gsec from its own directory, you should type ./gsec instead of just gsec. The current directory is usually not part of the search path, so plain gsec may either fail or launch a "wrong" gsec.
Changing the SYSDBA password
One Firebird account is created automatically as part of the installation process: SYSDBA. This account has all the privileges on the server and cannot be deleted. Depending on version, OS, and architecture, the installation program will either
- install the SYSDBA user with the password
masterkey(actually,masterke: characters after the eighth are ignored), or - ask you to enter a password during installation, or
- generate a random password and store that in the file
SYSDBA.passwordwithin your Firebird installation directory.
If the password is masterkey and your server is exposed to the Internet at all – or even to a local network, unless you trust every user with the SYSDBA password – you should change it immediately using the gsec command-line utility. Go to a command shell, cd to the Firebird \bin subdirectory and issue the following command to change the password to (as an example) icuryy4me:
gsec -user sysdba -pass masterkey -mo sysdba -pw icuryy4me
Notice that you specify sysdba twice in the command:
- With the
-userparameter you identify yourself as SYSDBA. You also provide SYSDBA's current password in the-passparameter. - The
-mo[dify]parameter tellsgsecthat you want to modify an account – which happens to be SYSDBA again. Lastly,-pwspecifies the type of modification: the password.
If all has gone well, the new password icuryy4me is now encrypted and stored, and masterkey is no longer valid. Please be aware that unlike Firebird user names, passwords are case-sensitive.
Adding Firebird user accounts
Firebird allows the creation of many different user accounts. Each of them can own databases and also have various types of access to databases and database objects it doesn't own.
Using gsec, you can add a user account as follows from the command line in the Firebird \bin subdirectory:
gsec -user sysdba -pass masterkey -add billyboy -pw sekrit66
Provided that you've supplied the correct password for SYSDBA, a user account called billyboy will now have been created with password sekrit66. Remember that passwords are case-sensitive.
Firebird 2.5 also introduces SQL commands for user management. While attached to any database, SYSDBA (or co-admins, see below) can create, alter and drop users like this:
create user sonny password 'cher_ie' alter user sonny password '9hgf72354b' drop user sonny
Other parameters for CREATE/ALTER USER are FIRSTNAME, MIDDLENAME and LASTNAME. Like PASSWORD, they all take a string argument.
Ordinary Firebird users can alter their own account details with gsec (gsec -user toby -pass hEltoPay -mo toby -pw purgaToby) and with SQL (alter user toby password 'purgaToby'). Only the account name itself can never be changed, not even by SYSDBA.
Appointing co-administrators
Note: What follows here is not essential knowledge for beginners. You can skip it if you like and go on to the Security section.
In Firebird 2.5 and up, SYSDBA (and others with administrator rights) can appoint co-administrators. In gsec this is done by adding the -admin
parameter:
gsec -user sysdba -pass masterkey -add bigbill -pw bigsekrit -admin yes gsec -user sysdba -pass masterkey -mo littlejohn -admin yes
The first command creates user bigbill as a Firebird administrator, who can add, alter and drop users. The second command grants administrator privileges to the existing user littlejohn.
The SQL equivalents of these commands are:
create user bigbill password 'bigsekrit' grant admin role alter user littlejohn grant admin role
To revoke administrator privileges with gsec, use -admin no. In SQL, use REVOKE ADMIN ROLE.
Notes:
GRANT ADMIN ROLEandREVOKE ADMIN ROLEare notGRANTandREVOKEstatements, although they look that way. They are parameters to theCREATEandALTER USERstatements. The actual role name involved here isRDB$ADMIN. This role also exists in regular databases; more about that in a minute.- Every user who has received administrator rights can pass them on to others. Therefore, there is no explicit
WITH ADMIN OPTION.
Differences between co-administrators and SYSDBA
- Co-admins can create, alter and drop users, but they have no automatic privileges in regular databases, like SYSDBA has.
- Unlike SYSDBA, co-admins must specify the extra parameter
-role rdb$adminevery time they invokegsecto add, modify, drop or view users. - Co-admins who want to use the SQL user management commands must specify the
RDB$ADMINrole when connecting. However, since nobody can connect to the security database, this requires a little trickery. First, the co-admin has to be granted theRDB$ADMINrole in at least one regular database as well. This is done in the usual way:grant rdb$admin to bigbill
RDB$ADMIN role in that database and has specified it while connecting. Every RDB$ADMIN member in a database can pass the role on to others, so again there is no WITH ADMIN OPTION. Once the co-admin has obtained the role, he can connect to the (regular) database with it and use the SQL user management commands. It's not the most elegant of solutions, but that's how it works.
Please remember:
The RDB$ADMIN role in a database gives the grantee SYSDBA rights in that database only!
- If it is the security database, the grantee can manage user accounts, but gets no special privileges in other databases.
- If it is a regular database, the grantee can control that database like he was SYSDBA, but again has no special privileges, and has no user administation privileges.
Of course it is possible to grant a user the RDB$ADMIN role in several databases, including the security database.
Security
Firebird 2.5 offers a number of security options, designed to make unauthorised access as difficult as possible. Be warned however that some configurable security features default to the old, "insecure" behaviour inherited from InterBase and Firebird 1.0, in order not to break existing applications.
It pays to familiarise yourself with Firebird's security-related configuration parameters. You can significantly enhance your system's security if you raise the protection level wherever possible. This is not only a matter of setting parameters, by the way: other measures involve tuning file system access permissions, an intelligent user accounts policy, etc.
Below are some guidelines for protecting your Firebird server and databases.
Run Firebird as non-system user
firebird by default, not as root. On Windows server platforms, you can also run the Firebird service under a designated user account (e.g. Firebird). The default practice – running the service as the LocalSystem user – poses a security risk if your system is connected to the Internet. Consult README.instsvc in the \doc sub-directory to learn more about this.
Change SYSDBA's password
masterkey, change it.
Don't create user databases as SYSDBA
gsec as shown above, or with any third-party Firebird administration tool.
Protect databases on the file system level
Disable Classic local mode on Linux
security2.fdb. If this worries you (and it probably should), reserve file system access to the security database (and other databases, while you're at it) to the server process only. Users are then obliged to connect via the network layer. Don't remove the libfbembed library from your system, though: it contains the complete server engine used by your Classic or Superclassic server!
Use database aliases
frodo:zappa without having to know that the real location is frodo:/var/firebird/music/underground/mothers_of_invention.fdb. Aliases also allow you to relocate databases while the clients keep using their existing connection strings.
aliases.conf, in this format on Windows machines:
poker = E:\Games\Data\PokerBase.fdb
blackjack.fdb = C:\Firebird\Databases\cardgames\blkjk_2.fdb
books = /home/bookworm/database/books.fdb
zappa = /var/firebird/music/underground/mothers_of_invention.fdb
.fdb (or any other) extension is fully optional. Of course if you do include it, you must also specify it when you use the alias to connect to the database.
Restrict database access
DatabaseAccess parameter in firebird.conf can be set to Restrict to limit access to explicitly listed file system trees, or even to None to allow access to aliased databases only. Default is All, i.e. no restrictions.
DatabaseAccess is anything other than All, the server will refuse to open any databases outside the defined scope even if it has sufficient rights on the database files.
Choose your authentication model
Authentication parameter in firebird.conf.
Consider whether Windows administrators should have SYSDBA rights
Authentication was trusted or mixed, Windows administrators would automatically receive SYSDBA privileges in all databases, including the security database. In Firebird 2.5, this is no longer the case. This reduces the risk that administrators with little or no Firebird knowledge mess up databases or user accounts.
RDB$ADMIN role as described in the section Appointing co-administrators. If, on the other hand, you want to restore the automatic SYSDBA mapping as it was in Firebird 2.1, read the following instructions.
gsec -user sysdba -pass masterkey -mapping set
-mapping drop.
RDB$ADMIN role in that database, and issue the following SQL statement:
alter role rdb$admin set auto admin mapping
DROP instead of SET.
RDB$ADMIN role when invoking gsec or connecting to a database – at least not if they want to make use of their SYSDBA rights. If they specify any role at all – even an unexisting one – the automatic mapping will not work.
There are more security parameters, but the ones not mentioned here are already set to an adequate protection level by default. You can read about them in the 1.5 through 2.5 Release Notes and in the comments in firebird.conf itself.
Windows Control Panel applets
Several control panel applets are available for use with Firebird. Whilst such applets are not essential, they do provide a convenient way to start and stop the server and check its current status.
Firebird Server Manager
The Firebird Server Manager applet is included in the Firebird distribution. The option to install this applet is only available for Superserver.
Note: The applet is also usable for (Super)Classic, provided that Firebird runs as a service, not as an application. Since the installation dialogue won't give you the option to include the applet with a Classic server, you must, if you really want it:
- install Superserver first;
- copy the applet
Firebird2Control.cplfrom the Windows system folder to a safe place; - uninstall Superserver;
- install Classic;
- copy the applet back to the system directory.
This is a screenshot of the activated applet. Notice that the title bar says Firebird Server Control, although it is listed in the Control Panel as Firebird Server Manager.
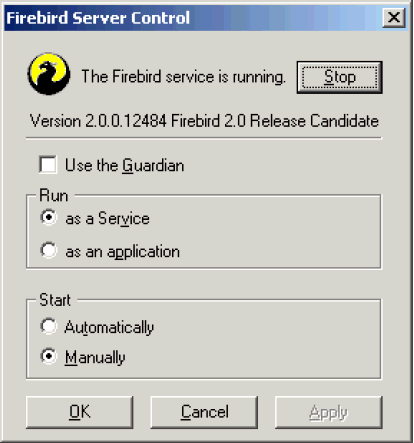
This applet only works on Windows NT, 2000/3/8, XP, Vista and 7.
Firebird Control Center
For an alternative to the bundled applet, you can visit this webpage:
https://www.achim-kalwa.de/fbcc.phtml
...and download the Firebird Control Center (FBCC). Please note that, unlike the applet included with Firebird, the Firebird Control Center will not work with Classic or SuperClassic servers. This may change in the future.
The current version – 0.4.2 – should work well under Windows 2000 and up. It offers the same functionality as Firebird's own applet, and more. An older release, still downloadable at https://www.achim-kalwa.de/dl/fbcc-0.2.7.exe, also runs under Windows 9x, ME and NT. Notice however that these Windows versions are no longer actively supported by the Firebird project, even if the engine runs on it.
Administration tools
The Firebird kit does not come with a GUI admin tool. It does have a set of command-line tools – executable programs which are located in the \bin subdirectory of your Firebird installation. One of them, gsec, has already been introduced to you.
The range of excellent GUI tools available for use with a Windows client machine is too numerous to describe here. A few GUI tools written in Borland Kylix, for use on Linux client machines, are also in various stages of completion.
Explore the Download > Tools > Administration page at https://www.ibphoenix.com for all of the options.
Note: Remember: you can use a Windows client to access a Linux server and vice-versa.
back to top of page
<< Installing Firebird | Firebird 2.5 Quick Start Guide | Working with databases >>







